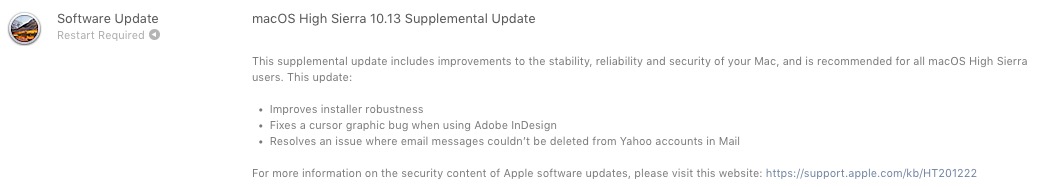
Apple a publicat recent un update suplimentar (Supplemental Update) foarte important pentru toti utilizatorii de Mac, care au instalat macOS High Sierra 10.13。
で macOS High Sierra 10.13 Supplemental Update いくつか解決しています。 Adobe InDesign の機能不全 そして1つ バグ できませんでした。 stergerea mesajelor primite in aplicatia Mail de pe conturi de Yahoo!。
この更新プログラムの最も深刻な部分は関連します。 2 つのセキュリティ問題, ce au venit “la pachet” cu noul sistem de operare High Sierra.
Vulnerabilitate parola criptare pentru APFS (Encrypted) – Disk Utility Bug
アプリケーションのバグ ディスク ユーティリティ それになります 表示パスワード フォーマットされたディスク ボリュームの APFS 暗号化。
Pe scurt, atunci cand introducem parola de criptate pentru un volum, aceasta este ceruta de doua ori, pentru a fi siguri ca nu am tastat-o gresit prima data. Apoi avem sa ne alegem un “ヒント” (un cuvant sau o fraza) ca indiciu pentru parola. Bug-ul din ディスク ユーティリティ, face ca parola sa fie vizibila in locul cuvantului sau frazei de la “hint”. In acest fel, este expusa oricarei persoane care are acces la Mac.
In video postat pe Twitter se vede exact cum se poate afla parola unui volum criptat APFS, cu ajutorul Disk Utility.
Would be interesting why Apple recommends erasing when diskutil can clear hints:
diskutil apfs setPassphraseHint [diskXsX] -user disk -clear pic.twitter.com/0khrm8aTq9— Felix Schwarz (@felix_schwarz) October 5, 2017
Vulnerabilitate Keychain Access – bypass user password
In mod normal si obligatoriu, cand accesam アカウントとパスワードをキーチェーンに保存, ne este ceruta ユーザー パスワード Mac. Printr-o vulnerabilitate a MacOS 高シエラ, o aplicatie rau-intentionata poate キーチェーン アクセスで salvate extrage parolele, sarind peste parola de user Mac prin intermediul unui click sintetic. Fals / simulat.
Released October 5, 2017
StorageKit
Available for: macOS High Sierra 10.13
Impact: A local attacker may gain access to an encrypted APFS volume
Description: If a hint was set in Disk Utility when creating an APFS encrypted volume, the password was stored as the hint. This was addressed by clearing hint storage if the hint was the password, and by improving the logic for storing hints.
CVE-2017-7149: Matheus Mariano of Leet Tech
安全
Available for: macOS High Sierra 10.13
Impact: A malicious application can extract keychain passwords
Description: A method existed for applications to bypass the keychain access prompt with a synthetic click. This was addressed by requiring the user password when prompting for keychain access.
CVE-2017-7150: Patrick Wardle of Synack
New downloads of macOS High Sierra 10.13 include the security content of the macOS High Sierra 10.13 Supplemental Update.
Asadar, daca aveti macOS High Sierra 10.13, este foarte recomandat sa faceti update-ul suplimentar. Acesta este disponibil via Mac の App Store, in tab-ul “更新“(si nu va schimba numarul versiunii). Apple a publicat deja macOS High Sierra 10.13.1 pentru developerii ce au device-urile in Apple Beta Software Program.







1 「セキュリティの問題APFS暗号化されたキーチェーンアクセス、MacOS High Sierra 10.13補足アップデートで解決されました」